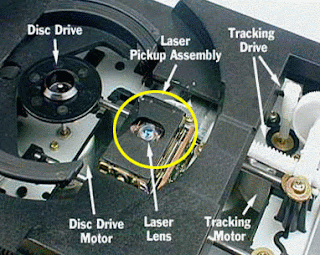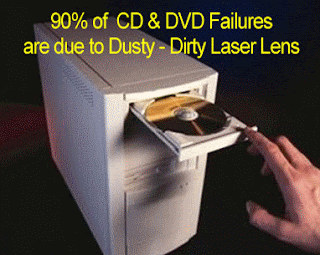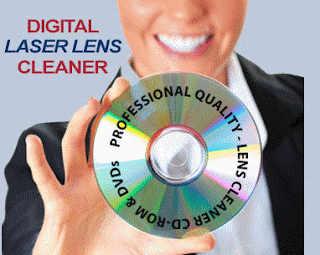
You really have no choice except a laptop, if your job or lifestyle takes a lot of trips each year. Their own laptop will help you a lot when you are away. Of your home or office
Nowadays, you can get laptops as powerful as desktop computers. Laptops are. With high resolution graphics, CD / DVD recording, large hard drives and even more features
However,
if you are sitting on the fence and portability is not needed even more
on the purchase of desktop taking into account the following reasons:
Desktops
are more durable than laptops: - Desktop computers are simply easier
expansion and update (with USB and FireWire ports), especially the CPU
and graphics card, even if you turn off multiple devices can hang a modern laptop.
Desktops are cheaper than laptops: - Desktop is even cheaper than a laptop, if you do not need it, why pay so much. Go to the side of the fence office, which is cheaper and convenient for you.
Laptop
repair is much more expensive than desktops: - For example, if your
sound card is not any reason you can easily replace it with an
inexpensive adapter. However,
if your laptop creates such a sound card problem, you must take your
wallet, because you will not be able to fix itself, and the whole
motherboard inside the unit must be replaced.
There is also how to buy it as soon as you making?
Processor:
- if you want to use your machine for standard office tasks and web
browsing, does not matter, it will have a processor. But if you are a serious gamer or if you need more power, the Intel Core 2 Duo chip, then you better.
Memory: - How much memory is installed in your PC, you will be able to run as many application at once. Upgrading
memory in a desktop computer after purchasing the PC is a breeze, but
in fact its good buy, the amount of memory you have installed the system
happy.
Motherboard: - provide a new motherboard you would for a smooth new technologies that are missing today. It would be faster, have the second-generation SATA ports, HD audio, and even a dual graphics card. You
must keep in mind to check whether the motherboard you buy two or USB
ports facades or not, due to plug the USB and digital audio players,
etc.
Graphics: - Before you go to look at this type of card in your PC suite. If you are a serious gamer and can pay as go for dual graphics card. There are two types of cards, which is removable from the card and the other is soldered onto the board. However, we recommend a discrete graphics card for gaming and an integrated graphics solution for other purposes.
Sound
Card: - for office use, you must purchase an integrated sound card of
your PC, but if you want a PC in your home, then a dedicated sound card
would be the best choice.
HDD:
- It is totally dependent on you, if you want to store large amounts of
data such as digital photos or multimedia files on your PC, hard drive
capacity, the ability to obtain more information. For normal use, buy 40 or 80 GB that use the most users these days.